Data Security
Data security is of utmost importance to the integrity of research. There are two ways in which to secure your data. If data is kept in a physical manner (i.e. lab notebook, paper surveys, etc.), then physical security is needed. Examples of physical security include lockable filing cabinets to hold the physical copies of data. If data is stored in an electronic manner (i.e., laptop, electronic database, cloud storage), then information security is needed. Examples of information security include the use of encryption and/or the UTK Secure Enclave, a system that is compliant with federal data security requirements and can be used to store sensitive data.
Although these are best practices, some sponsors may require additional physical and information security practices dependent upon the nature and sensitivity of the research and data.
Controlled Unclassified Information
| Controlled Unclassified Information (CUI) is information that the U.S. government creates or possesses, or that an entity creates or possesses on the government’s behalf, that is subject to safeguarding or dissemination controls. CUI was established by Executive Order 13556 and 32 CFR § 2002. These documents establish a uniform program for managing sensitive information. The program is overseen by the National Archives. The CUI program applies to many federal agencies, and can also apply to their contractors/grantees and subcontractors / subawardees. CUI does NOT include classified information. |
NIST Special Publication 800-171
CUI controls are specified by the National Institute of Standards and Technology (NIST) in NIST Special Publication (SP) 800-171 Rev 2, “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.” You can expect to see CUI controls noted in federal grants and contracts that involve Protected Health Information (PHI), Controlled Defense Information (CDI), and any other type of information defined as CUI by the federal government. Projects that are subject to NIST 800-171 requirements must be covered by a security plan that describes more than 100 physical and information system controls.
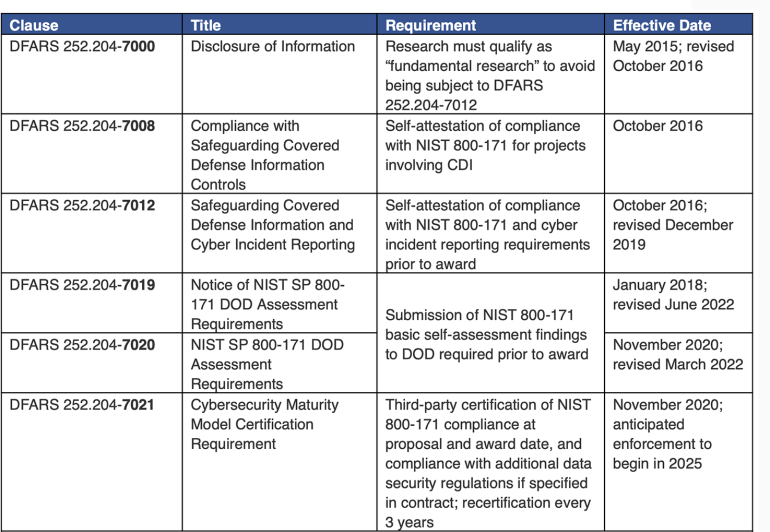
Research Funded by the Department of Defense (DOD)
When UTC receives a grant award or research contract (or subaward or subcontract) that is funded by a DOD agency, the award terms and conditions may include one or more data security clauses that are defined in the Defense Federal Acquisition Regulation Supplement (DFARS). DFARS clauses that are numbered “252.204-7###” establish specific data security and cybersecurity breach reporting requirements for researchers and their institutions. DFARS clauses that are applicable to DOD-funded research involving CUI include the following:
Options for Researchers Seeking to Participate in Projects Funded by DOD
To minimize the burden of compliance with DFARS 7000-series clauses, researchers can pursue the following strategies:
- Seek to obtain a “fundamental research” determination from the DOD Contracting Officer.
- When reviewing a Funding Opportunity Announcement (FOA) or Request for Proposal (RFP), note any guidance related to data security requirements, expectations that CUI/CDI or proprietary information will be used or generated, or if there will be restrictions on participation in the project based on citizenship. Contact the program officer or other point of contact identified in the FOA/RFP to determine whether your project can be scoped as fundamental research.
- Indicate in your proposal that the research you are proposing is intended to be disseminated in the public domain without restrictions. This does not guarantee that a DOD Contracting Officer will agree, but it clarifies your intent. The decision is ultimately up to the contracting officer.
- Emphasize and give examples in the proposal how the research that you are proposing has both civilian and military applications (“dual uses”).
- Assert in the proposal that the work you are seeking to perform qualifies as fundamental research in accordance with National Security Decision Directive 189; the Contracted Fundamental Research memo from the Undersecretary of Defense dated June 26, 2008; and the Fundamental Research memo from the Undersecretary of Defense, dated May 24, 2010. This assumes that you have not entered into a non-disclosure or confidentiality agreement with any project collaborators that will result in publication restrictions or research findings being proprietary to another party.
- In your proposal, ask for the contracting officer to review UTC’s scope of work separately from that of any collaborating organizations, and to determine whether your work will qualify as fundamental research as defined in DFARS 252.204-7000(a)(3).
- Be cautious when proposing to serve as a subcontractor to a defense contractor funded by DOD. Even if a DOD Contracting Officer scopes your part of the project as fundamental research, this designation will be lost if the defense contractor specifies in the subcontract document that the information you generate in performing your scope of work is proprietary to them.
- Use the UTK Secure Enclave to achieve compliance with DFARS 252.204-7012 and -7020. The High Performance and Scientific Computing (HPSC) group at UTK provides resources and support for research involving sensitive information through the Secure Enclave. The Secure Enclave protects PHI, CUI, and other types of sensitive information. The Office of Information Technology at UTK provides support, documentation, training, and support services for the Secure Enclave. Contact the UTC Office of Research Integrity or the OIT Help Desk for more information.
- Please note that researchers using the Secure Enclave will be required to develop a security plan that addresses the applicable controls set forth in NIST SP 800-171. The advantage of using the Secure Enclave is that many of the required controls are already implemented and can be “inherited” in your security plan. This reduces the burden of implementing and monitoring compliance with controls for you and your department.
- Achieve NIST 800-171 and DFARS compliance independently. This is a lengthy and expensive process and is not feasible without advance planning, development, and identification of funding sources to support the implementation of a compliant system and research environment. A system security plan that addresses all of the applicable NIST 800-171 controls will also be required.