Amani Altarawneh
Liveness analysis, modeling, and simulation of blockchain consensus algorithms' ability to tolerate malicious miners
A Dissertation Presented for the Doctor of Philosophy ;in Computational Science: Computer Science, The University of Tennessee at Chattanooga
Amani Altarawneh, August 2021
Abstract:
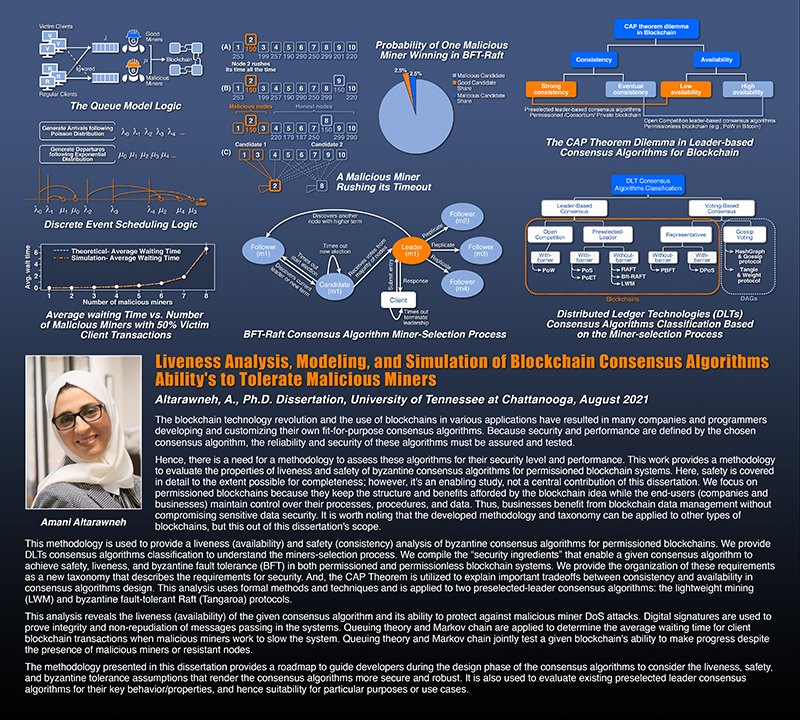
The blockchain technology revolution and concomitant use of blockchains in various applications have resulted in many organizations and individuals developing and customizing their own fit-for-purpose consensus algorithms. Because security and performance are principally achieved through the chosen consensus algorithm, the reliability and security of these algorithms must be both assured and tested. This work provides a methodology to assess such algorithms for their security level and performance is required; liveness for permissioned blockchain systems is evaluated. We focus on permissioned blockchains because they retain the structure and benefits afforded by the blockchain concept while end users maintain control over their processes, procedures, and data. Thus, end users benefit from blockchain technology without compromising data security. We expect that this methodology and taxonomy can be applied to other types of blockchains. The developed methodology is used to provide a liveness analysis of byzantine consensus algorithms for permissioned blockchains. We provide a Digital Ledger Technologies (DLTs) consensus algorithm classification to understand the miner-selection process. We compile the ``security ingredients'' that enable consensus algorithms to achieve liveness, safety, and byzantine fault tolerance (BFT) in blockchain systems. We organize these requirements as a new taxonomy that describes requirements for security. And, Brewer's theorem is utilized to explain tradeoffs between availability and consistency in consensus algorithm design. This analysis uses formal methods and techniques and is applied to two exemplary consensus algorithms: lightweight mining (LWM) and byzantine fault-tolerant Raft (Tangaroa). Our analysis reveals the liveness of the given consensus algorithm and its ability to protect against malicious miner denial of services (DoS) attacks. Digital signatures are employed to prove integrity and non-repudiation of messages passing in the systems. Queueing theory and Markov chains are applied to determine the average waiting time of client transactions when malicious miners work to slow the system. Queuing theory and Markov chains jointly are employed to test a given blockchain's ability to perform correctly despite the presence of malicious miners or resistant nodes. Overall, the methodology presented here provides a roadmap to guide developers during the design phase of consensus algorithms to render these algorithms more secure and robust.
Click here to access a copy of Amani's dissertation.